The threats – real and perceived
[First posted 10 September 2020; minor changes 21 June 2021]
Luckily, there’s plenty of advice and guidance available – often slanted particularly towards our demographic (ie oldies) …

Those two sites are particularly easy to follow and understand, but others are equally informative and targeted.
Your bank probably has guidance which it publishes online and which is accessible to everyone, not just their customers …
I’ll return to further information, guidance and references at the end of this post, but first we need to look at a few issues, discuss some terminology that’s widely used and try and tease out what’s really important, and what’s just an inconvenience and then it’s up to you to judge where you find yourself on the scale of …
Terrified -> Apprehensive -> Sensibly Aware -> Relaxed -> Unconcerned
First let’s distinguish the difference between online security and online privacy. These are two different issues which are however linked. Sometimes you have to relinquish some privacy to receive a service – unless you choose to pay for it (and I’ve long been an advocate of paying for services if they do a job that is necessary); exactly how much privacy are you prepared to relinquish?
Security on the other hand is an absolute – you should not be prepared to accept less than your very best efforts . We’ll deal with that in the third part of the post.
How do you relinquish your privacy, and how much of a loss of privacy is acceptable?
Some services could not be offered without income from adverts, or paid-for advertising – eg Facebook, Twitter and Instagram; and some eg Google and Amazon track and provide information to resellers if you don’t block them from doing so. As an example of how much value Google sees in getting knowledge of what you’re doing and where you’re doing it, they paid Apple $8bn recently to remain as the default search engine for any browser that’s running on an Apple device!
Incidentally, if you clicked on that link you might have been asked whether you wanted to accept cookies – what exactly are they, and what do they do. This article from Norton explains what they do quite well …
 Essentially, they record what you do on a website so that when you return to it some of the settings are remembered and applied. Cookies do however also have a downside in that some can also act to track your activity once you’ve left the site. For that reason, you should disable in your browser the ability of third-parties to glean information from a cookie, and also to prevent them tracking your activity once you’ve left the site. You can at anytime, clear the cookies from your browser, and indeed on some internet browsers set them up to delete cookies when you leave (close the window) the site. The browser I use – Firefox – alerted me the first time I went to the site to the fact that Norton was using a Fingerprinting cookie itself …
Essentially, they record what you do on a website so that when you return to it some of the settings are remembered and applied. Cookies do however also have a downside in that some can also act to track your activity once you’ve left the site. For that reason, you should disable in your browser the ability of third-parties to glean information from a cookie, and also to prevent them tracking your activity once you’ve left the site. You can at anytime, clear the cookies from your browser, and indeed on some internet browsers set them up to delete cookies when you leave (close the window) the site. The browser I use – Firefox – alerted me the first time I went to the site to the fact that Norton was using a Fingerprinting cookie itself …
Another thing you should consider is whether you want adverts to be shown, or not. You might get a request to enable adverts when you visit a site, the answer you supply will be held in a cookie in the browser – that’s how cookies work. Firefox, Brave and Microsoft Edge, by default, block most, if not all, adverts. These are often annoying and having a browser that blocks adverts, or if you use Chrome – using an ad-blocker like AdBlock Plus often makes for a more “pleasurable browsing experience” by limiting the intrusion you might feel upon your privacy.
Which brings us to browsers and search engines
Search engines are not created equal! Whilst Google is often thought to be the same as the internet and is often mistaken to be an internet browser itself, it is in fact just one of a range of possible search engines that you can use to look for information on the internet. It uses a platform called Chromium to display the results of its searches to you through a browser called Chrome. However, other browsers – Microsoft’s new Edge, Brave and Opera all use the same underlying Chromium technology – the difference being they don’t track what you’re doing “to present the content that most meets your needs” (Google’s philosophy) and in some cases (eg Brave) they can actually prevent tracking of your browsing history. For the reasons given above, I use either Brave or Firefox as my internet browser and I’m leaning more to the latter nowadays as it seems quicker and more secure as well.
So what safe and private search engine could you use as an alternative to Google. I use DuckDuckGo …
… but others I could have used might have been Bing, Yahoo or another one you might choose from this article or the list of other articles at the end of it …
There are many specialist search engines (as explained in the above article) that can give you much better, and more targeted results than a broad-spectrum Google search.
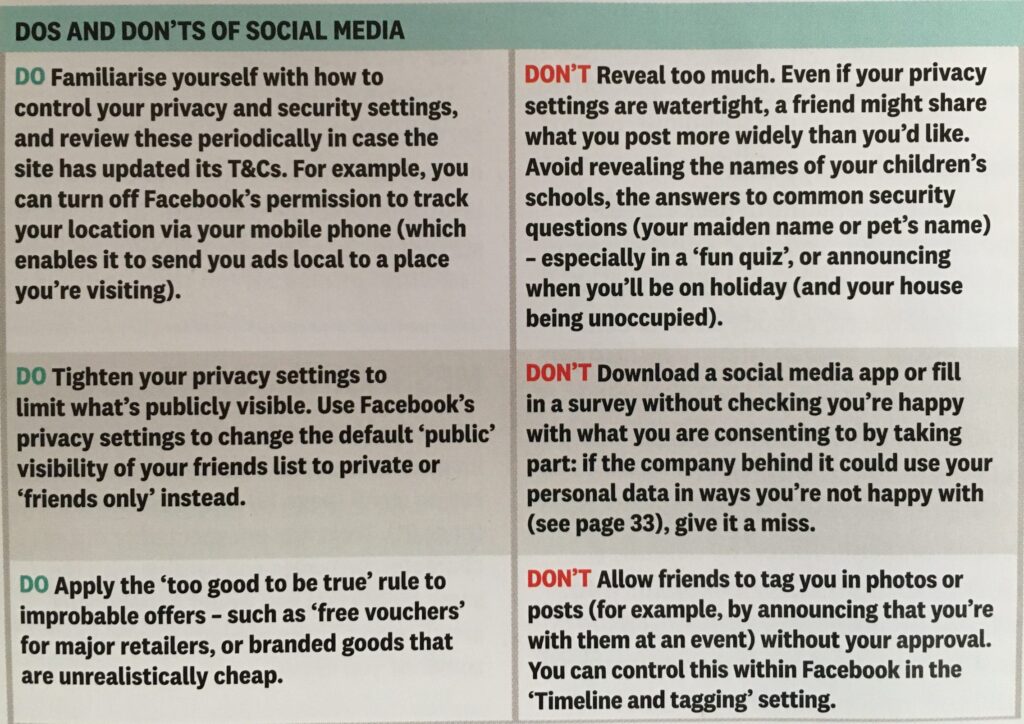
Finally, no discussion of Privacy can ignore Social Media and Facebook in particular. These applications, if left to their own default settings, are effectively personal information mining engines. They grab what information they can from you, and sell it on to whoever is willing to pay for it; or are indeed the platform for data mining, vis the Cambridge Analytica affair. Online retailers are not exempt from this and Amazon for instance has a wonderful record of your browsing history! Are you sure you know what it’s doing with that information? So look at this table taken from a recent Which? supplement – Staying Secure in a Digital World – and just check whether you need to change your settings if you use any Social Media apps …
So that’s Privacy dealt with.
Should you be frightened?
The take away message I want you to have is Frightened – no; cautious – yes!
Online banking is very secure – a recent survey in Which? produced the following scores …
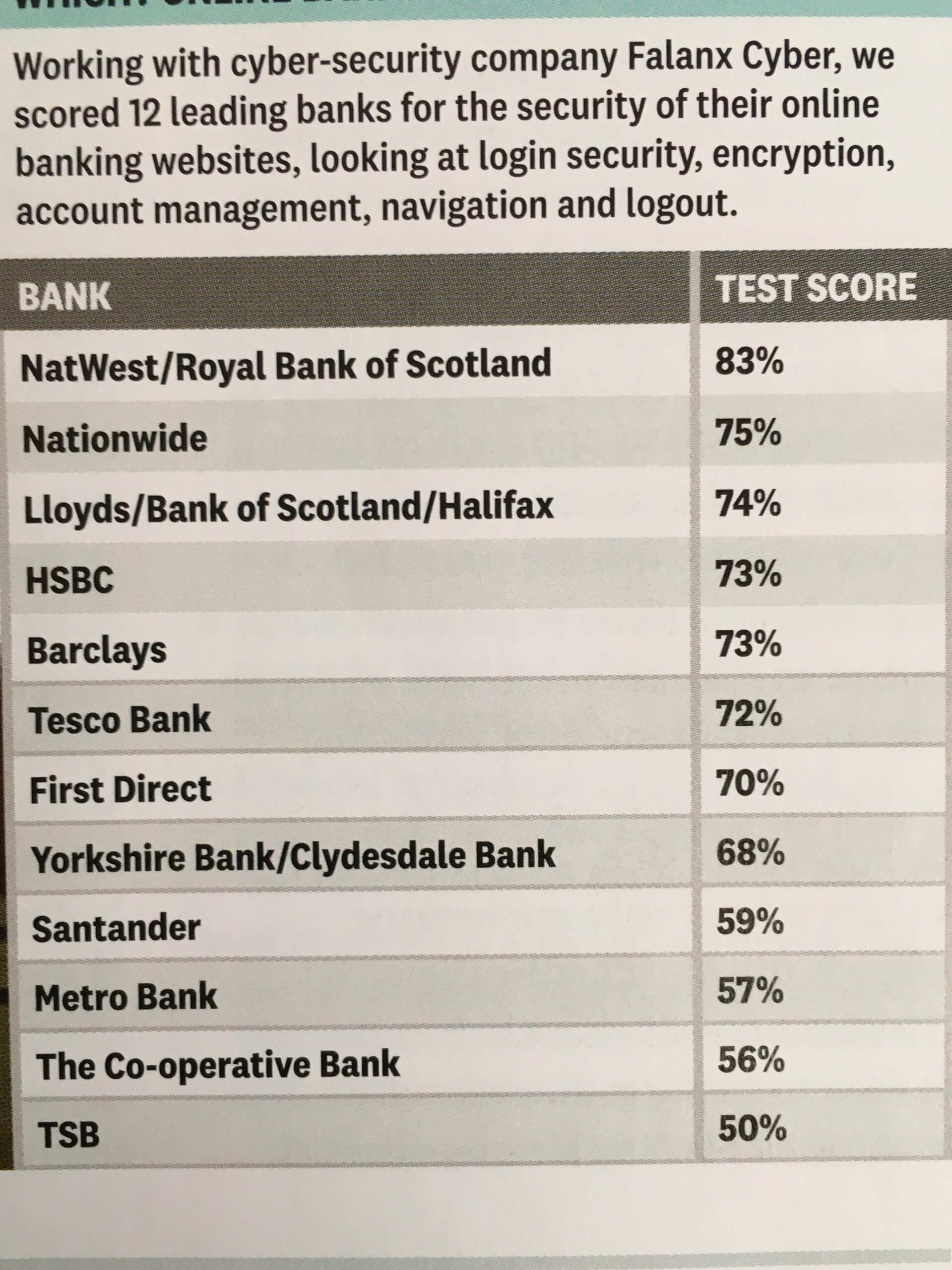
… plus you are protected and most of the banks are increasingly opting to adopt an online and mobile guarantee to refund you where you’ve been the innocent victim of a fraud. Here for instance is Barclay’s “Online and Mobile Banking Guarantee.”
They really don’t want to shell out money, so they are trying to educate us to be wise to scams. So let’s take a scam test …
Banks are also often supplying software free (or at reduced cost) for you to install to protect your machine, to protect you from fraud – and of course themselves from having to pay out! I was recently offered a piece of software called Malwarebytes by the NatWest and although I have an Apple Mac computer which are well known to be relatively secure from Viruses, Spyware, Trojans and other malware, I installed it. I was pleased to note that I didn’t have any malware on the machine.
Surprisingly you might think … it’s safer to use the mobile app on your phone, or tablet to do online banking and retail purchases than a web browser. This is because the app on the mobile device has to be verified by Google for Android (Google Play Store) or Apple for iOS/iPadOS (Apple Store). Whereas a browser could be infected, or compromised with malware. [That’s something I’ve learnt whilst preparing this post!!!]
When you’re out and about and NEED to do an online transaction from your mobile – use cellular rather than WiFi. The latter can be really open to “sniffers”. [I must admit I try to avoid doing online transactions when away from a domestic network.]
Whilst we’re at it, you might like to think about doing a Detox on your phone, and even consider installing Firefox as the browser of choice rather than Chrome (Android) or Safari (Apple) on your mobile device …
So we come to phishing and pharming, vishing and smishing – I kid you not! We’ll leave aside spear phishing because we’re not important enough for that – it’s used to target “corporations” and individuals within them! [Please excuse me not going into details on any of these. You can follow the links for further information.]
However the most scary scam I’ve been made aware of is one that befell a member of my family when they were distracted sufficiently to become the victim of SIM swapping.
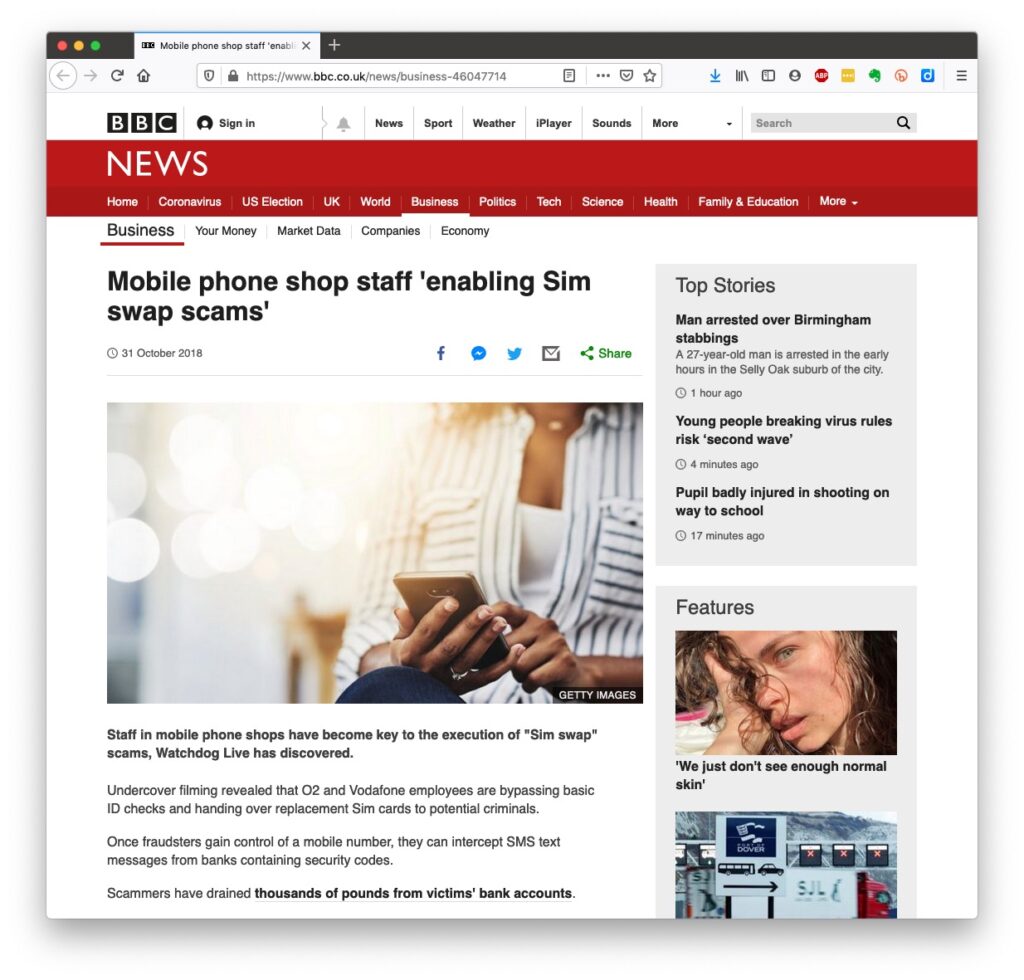
I discussed this with the Cardiff U3A Computer Group last June and you can read the updated post here.
What should you do to protect yourself?
Some of these pieces of advice are really quite straightforward, but some require some intervention by yourselves.
- Keep your operating software up to date. This is particularly true if you’re a Windows user, and even more true if you are still running an older version of Windows than Windows 10. If you’re using Windows XP, Windows Vista or even Windows 7 you should seriously consider disconnecting your machine from the internet because even if you’ve got anti-malware software running this is probably not protecting you against the latest threats.
- Install anti-malware, or anti-virus software, particularly if you’re a Windows user. Don’t pay more than you need to. Windows Defender from Microsoft is Free and for our demographic relatively undemanding and unsophisticated users, more than sufficient. Keep it up-to-date as well! [As I said previously, your bank might be offering free software as well.]
- Keep the software you use regularly up to date as well. Consider removing any software from your machine that you don’t use – this is because software vulnerabilities are discovered sometimes quite a while after the software was first released. It will also save you disc space!
- Be cautious over installing extensions into your browser. These are often extremely useful and valuable tools, ie password managers, Dropbox, note taking, Google Back up and Sync, but if you don’t get them from the official sources then you might be importing vulnerabilities, eg spyware and trojans to your system.
- Very seriously consider logging-out from social media and other retail sites when you’ve finished using them, especially Facebook, you just don’t know what tracking and logging of what you do, even where you are, if you leave yourself logged in on a mobile device.
- Free software is both a boon and a curse. Only download open source software from a reputable site such as Softpedia, and never try and get proprietary software for free. Read this article about Free download sites if you want to know more.
- Remember the golden rule 1 – if it seems too good to be true, it probably is, so steer clear!
- Remember the golden rule 2 – don’t speak to strangers (an oldie but goldie that one); in other words if you don’t know where an email has come from – ignore it; if the website address looks a little strange – do an internet search on the company or organisation to check if the address you’re looking at is a spoof of the proper one.
- Have more than one email address. Use one as your personal address, then use other ones that you can “throw away”when you need to register to a website, but you’re unlikely ever to go back to it again. Or have an email address (UserID) specifically for online purchases. Splitting things like this reduces the risk of you being the victim of fraud.
- Seriously consider using an email service that is NOT connected to your Internet Service Provider (ISP). If you decide to change your ISP, and you should review them periodically, then you will have real problems if your email address is linked to their service!
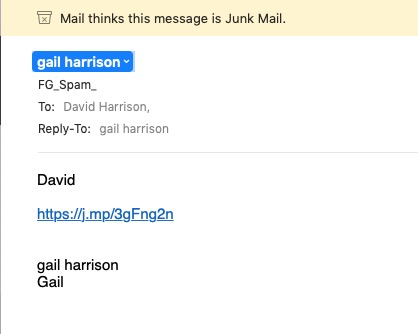
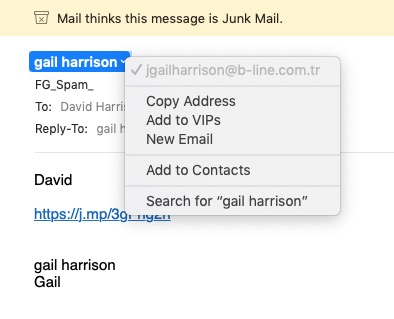
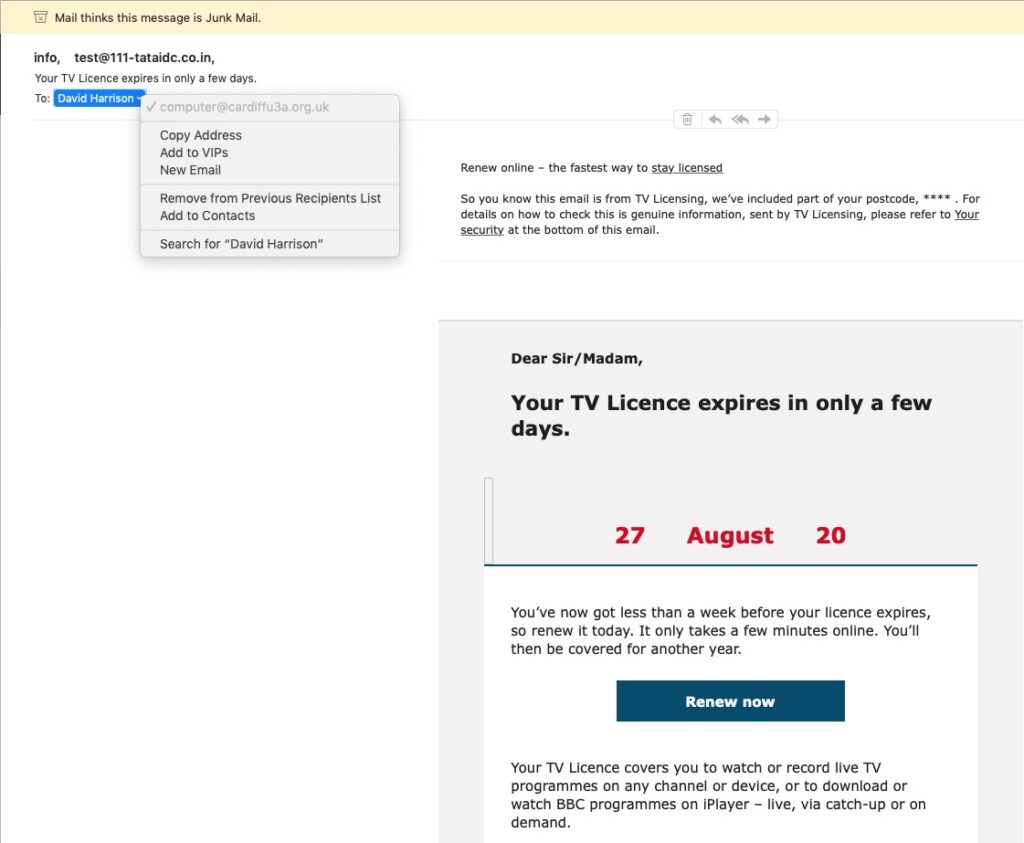
- You’ve got Spam filters running? Of course you have – but you better check! Probably your ISP, or email provider (eg Gmail, Yahoo, Microsoft Outlook or Hotmail) is filtering out what it thinks is spam, but occasionally some gets through. If that’s the case then you can always look at the real sender of your message. Take a look at the examples below …
You can also apply filters to divert incoming email into different folders in your email system. That reduces the amount of Junk that you need to review. [I’ve also advocated using the “native” email application for your device rather than rely on the web-based service the email provider has. Thus on a Windows device – use Windows Mail (or Outlook); on a Mac use Mail. You can then easily synchronise your email between devices from multiple email accounts. Tidy!]
So we come to Passwords …
… this is the point at which you need to consider intervention and changing your behaviour! You might also need to do a fair bit of work, but it’s worth it if you want to have a secure internet experience.
Let’s just see what using an insecure Password can lay yourself open to. Type in the word Password, or ABC123 from the link above – frightening eh!?
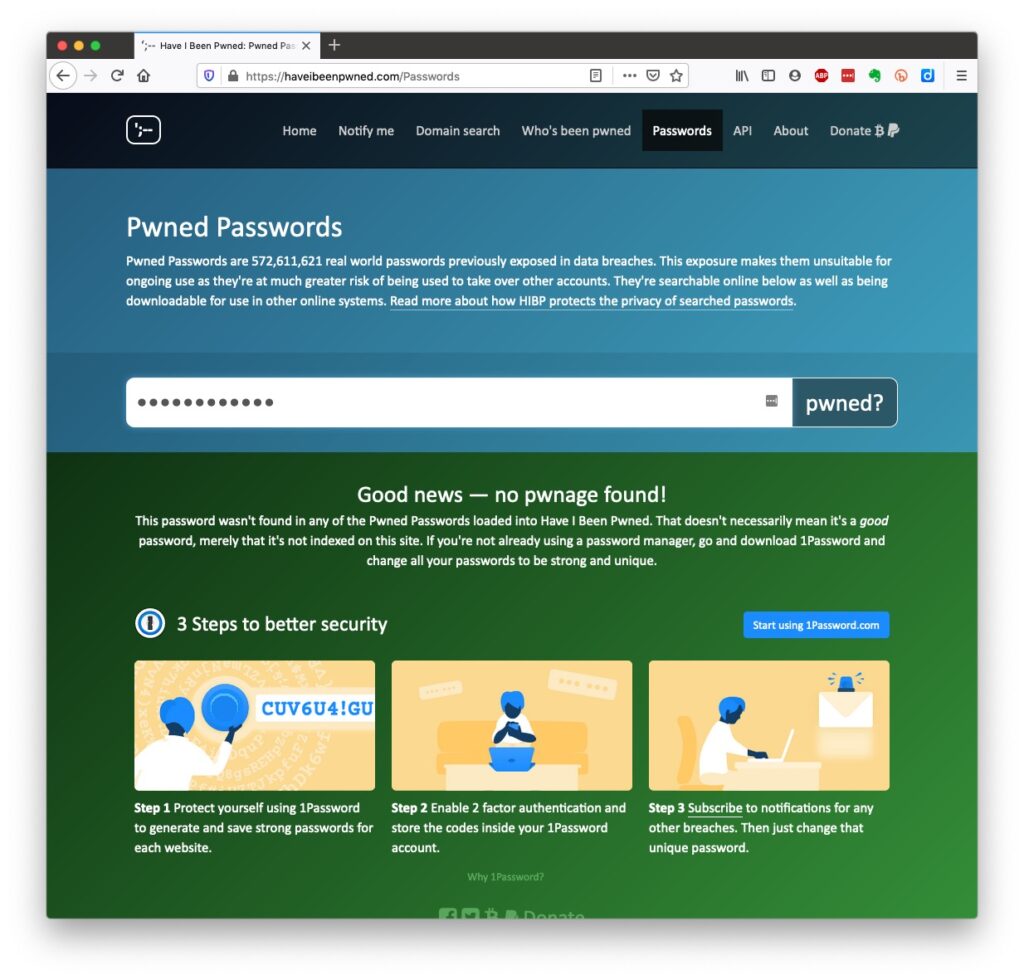
What about the combination of your email address with your password – has that been “pwned” (ie stolen through a data breach)? Try typing your email address into the link above.
And if you want to see a list of which websites have been breached, it’s alarmingly long!
So … use a unique password for everywhere you sign on. There’s lots of tricks to achieve this; some of which I wrote about in a post quite a long time ago …
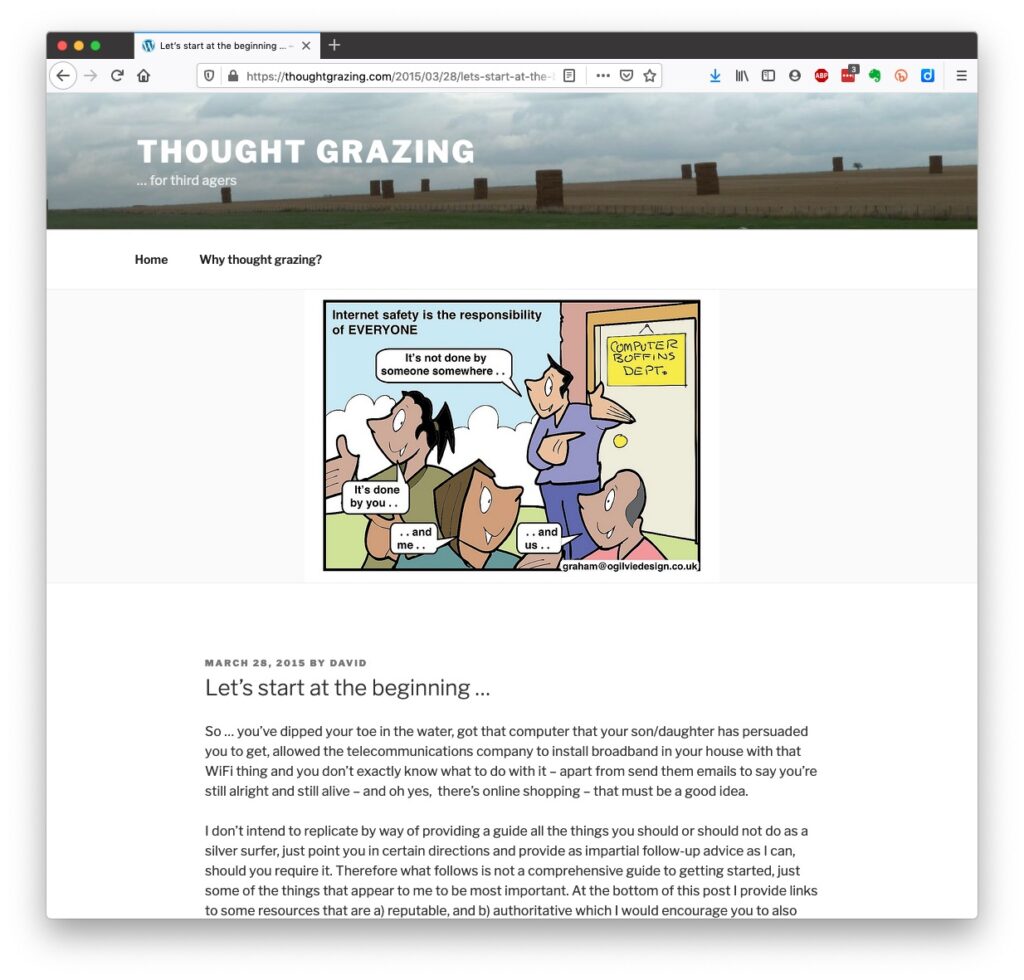
… but the real change of behaviour is to use a Password Manager – again I wrote about this a little while ago and linked it to using Two Factor Authentication, which is also covered in the same post …
Password managers
I use LastPass, but other common ones are Dashlane and 1Password. Please make up your own minds after reading some Reviews and seriously consider using one.
Slides from talk given to Bridgend U3A
Keeping safe online
Slides from talk given to Cardiff U3A
Staying safe online
References


… but these are available … Which? webpages – Scams & older people
I seriously do recommend signing up for the Which? Scam Alert Service – sign up for an email alert – and I seriously recommend you NOT broadcasting other people’s warnings to you about scams; they could be old, they could be inaccurate, they could be scams in themselves.
Look on the Age UK webpages – Staying safe in your digital world and specifically How to stay safe online
Your bank will undoubtedly have Internet Security webpages. Mine has a Security Centre web presence and particularly they provide a number of Fraud Guides
I could give a million references to changing your privacy settings on Social Media, but here are a couple relating to Facebook, perhaps the most challenging service of the lot.
First – what Facebook unchallenged will want to get from you. You are able to disable (prevent) all or some of these … Sign up for Facebook – this is not sign-up site, it’s just one to educate you on the privacy you might give up without realising before you sign up (but of course you can run the checklist at any time); then How to change settings on Facebook and finally Securing Facebook: Keep your data safe with these privacy settings.